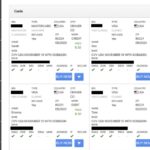
This stolen information is then used to create counterfeit credit cards or make fraudulent online purchases. The term “dump” refers to the act of extracting the data from the credit card’s magnetic strip or chip. The supply chain for carding stores like Joker relies on large data breaches, usually sourced from hacks involving point-of-sale software for large retail or merchandise outlets.
But the darkness of these deals doesn’t perfectly hide criminals from accountability. The local FBI office says even criminals buying and selling from other countries are being caught. Collins said, “We arrested someone in Romania and had them extradited to Utah.” The FBI showed us sites on the dark web, one of them listed the items for sale complete with photos, descriptions, guarantees and even seller star ratings. Harris said, “this particular seller has a rating of 4 and a half out of 5 stars. So, it appears they have been doing this for a while and have some good customer service.” Alex Herrick is a seasoned web designer and digital strategist with over a decade of experience in the industry.
Dangers And Risks Of Credit Card Dumps
Unbeknownst to them, the skimmer is quietly at work, copying the credit card details of each transaction. This stolen credit card data includes the cardholder’s name, card number, expiration date, and, in some cases, the Card Verification Value (CVV). B1ack is notorious in these forums for distributing CCS/FULLZ—credit and debit cards along with full personal information, known as “FULLZ,” which contains enough data to commit identity theft or fraud—as freebies. Further investigation indicated that B1ack started this marketing campaign in January this year by posting hundreds of free stolen payment cards to build credibility and attract more customers. This massive data breach highlights the importance of businesses taking a proactive approach to cybersecurity to prevent similar incidents in the future. The connection between credit card dumps and identity theft is both undeniable and alarming.
- B1ack’s Stash’s emergence and rapid growth highlight the ongoing evolution of dark web marketplaces and the persistent threats they pose to global cybersecurity.
- Those involved in credit card dump activities can face criminal charges, leading to fines, imprisonment, or both.
- The process begins with the theft or purchase of credit card information, which includes the cardholder’s name, credit card number, expiration date, and CVV code.
- Dark Web credit card fraud is an ongoing problem and is not showing any signs of going away.
- Now, it seems the next avenue is giving universal access to all citizens, starting with ChatGPT Plus.
How Many Cards Are Still Active?
Point-of-sale card skimmers, targeted Magecart attacks on websites and info-stealing trojans are among their top tools for stealing credit-card data. Dark web monitoring platforms, such as Lunar, provide an automated solution to safeguard personal identifiable information (PII) and credit card details. These platforms continuously scour the deep and dark web, looking for any traces of your sensitive information.
Advertising Carding On Legitimate Platforms

The site also has a unique news section, listing new leaks and their size. The threat actor initially focused on giving away freebies but eventually began promoting their shop on various dark web forums on April 16, 2024, ahead of their major launch at the end of April. See my tips and best picks on how to protect yourself from identity theft by searching “identity theft” at CyberGuy.com by clicking the magnifying glass icon at the top of my website. Learn how to automate financial risk reports using AI and news data with this guide for product managers, featuring tools from Webz.io and OpenAI. Freshtools was established in 2019 and offers various stolen credentials, accounts, and host protocols like RDP. It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products.
Australia And New Zealand Threat Landscape In H1 2025 Is Worrying, But Has A Silver-Lining
Its presence across multiple dark web forums, coupled with an active Telegram channel, indicates a calculated effort to build trust and legitimacy within illicit communities. The technique of making free data available to promote a site is nothing new, other well-known carding marketplaces, such as BidenCash and Joker’s Stash, operate similarly. A vast majority of bank and credit card apps offer notifications and alerts for questions about suspected fraud. Torzon Market has established itself as a significant player in the darknet ecosystem, offering a secure, user-centric platform for anonymous trading.

Leveraging Outseer FraudAction Compromised Credit Card Feeds
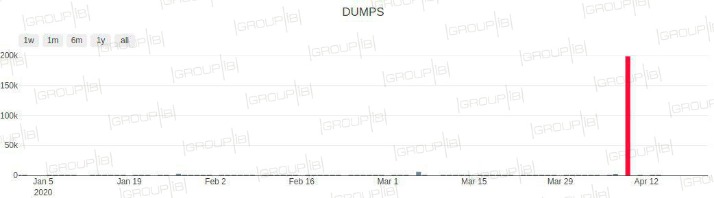
Indeed, in the last six months of 2020 alone, threat actors offered more than 45 million compromised cards for sale in underground credit-card markets monitored by security firm Cybersixgill, the company said in a report. These cards are then used by cybercriminals to make online purchases, including buying gift cards, that are hard to track back to them. One particular form of credit card fraud that has gained notoriety is known as “credit card dump.” In this article, we will explore what credit card dump is, how it works, and the impact it has on individuals and businesses. We will also discuss preventive measures that can be taken to protect against credit card dump attacks.
About Cyberint
“Collecting and storing personal information that is not reasonably necessary to your business breaches privacy and creates risk,” she said. Information and Privacy Commissioner Angelene Falk urged all organisations to review their handling of personal information and data breach response plans. Our platform alerts security teams when an organization’s sensitive data is found.
This enables systems to detect fraud based on minute changes in transaction velocity, merchant category patterns, and even the time of day purchases are made. Pattern recognition through machine learning has revolutionized how we spot compromised cards. Businesses pass fraud-related costs on to consumers through higher prices. When fraudulent transactions occur, merchants frequently end up eating the costs through chargebacks. Payment information moves through a series of specialized dark web markets. The data then gets parsed, sorted by bank type and location, and sold in batches.
“Fullz” Is The Word Cybercriminals Call A Complete Info Grab
Consumers may face financial losses due to unauthorized charges on their accounts or even identity theft. In the case of identity theft, thieves might use stolen credit card information to open new lines of credit or apply for loans, potentially damaging a consumer’s credit score and causing long-term financial harm. Additionally, consumers may need to spend considerable time and resources to resolve the issue and restore their financial wellbeing. It has built a reputation for being a reliable source of stolen credit card data and PII.

Criminals obtain this data through various methods, such as skimming or hacking into payment systems. Once obtained, the stolen credit card data is resold to other individuals or criminal organizations on the dark web. When credit card data is dumped, it often ends up on the dark web, where it’s bought and sold by criminals. The information can be used in multiple ways, such as making unauthorized purchases or even creating counterfeit cards for further criminal activities.
How War Impacts Cyber Insurance
One particularly interesting detection method involves monitoring dark web markets themselves. I’ve worked with family-owned businesses that nearly went under after getting hit with a wave of fraudulent purchases. One compromised payment processor or e-commerce platform can yield thousands of card numbers at once. However, in order for its services to gain more traction, BidenCash decided to release details for more than 1.2 million cards in one go. Contrary to popular belief, most carding platforms no longer hide in the dark web (i.e. the Tor network).
In this section, we’ll explore what steps companies should take when faced with a credit card data breach, as well as how they communicate with affected customers. Companies, on the other hand, face significant reputational damage and potential legal consequences when dealing with credit card dumps. A successful breach could result in a loss of customer trust, which can negatively impact sales and revenue.