Easily initiate data encryption on your external drives and disks, ensuring compliance with your specific company policies. Encryption-2-Go offers controlled encryption, container-based or directory encryption, and even detects existing BitLocker To Go encrypted drives. With configurable user selection dialogs, it provides a user-friendly experience while maintaining strict security. As you discover the hidden depths of the web, ensure your sensitive data remains protected, no matter where it travels. Ahmia emerges as a robust dark web search engine offering more than just search results.
- Riseup is a volunteer-run social movement organization that offers email, email lists, a VPN, online chat, and other online services for political activists engaged in various causes.
- While not an onion site, Tor Metrics can provide a fascinating peek “under the hood” of the dark web.
- Users play a crucial role in shaping the platform, reporting abusive or inappropriate content to ensure a safe and relevant browsing experience.
- We are not responsible for any harm or loss you may receive by following links listed on this site.
- They store all bitcoins encrypted and large amounts in cold storage to protect from hackers.
- During my tests, ExpressVPN’s military-grade encryption and verified no-logs policy provided consistent protection against tracking and monitoring.
Best Anonymous Dark Web Browsers On The Tor Network
Device spoofing and browser fingerprinting evasion to appear legitimate. Carding attacks not only cost money but also erode customer trust, damage reputations, and trigger legal consequences if not addressed properly. PatrickStash has two categories, Cards and Cards NoVBV (short for Verified By Visa).
- The information shared on this platform is designed to keep out any curious or inexperienced actors.
- ProPublica is a prominent investigative journalism platform on the regular and dark web.
- Validated cards are used to purchase goods or services, resell digital items, transfer funds to mule accounts, or, sold to other criminals in darknet marketplaces.
- Accounts come with free proxies and displayed at home page with info like country, account type, balance, price, and order link.
- Wasabi Wallet isn’t free to use, but, for a small fee, you get reliable and anonymous cryptocurrency transactions.
- Facebook’s onion mirror allows people to access it in countries that block the platform, allowing people to connect across digital borders.
Email Services
It often hosts copyrighted materials without permission, violating many countries’ copyright laws. Downloading or distributing such material is against the law and can have legal consequences. While they might sound the same, these websites are fundamentally different.
Subscribe To Our Blog For More News And Updates!

Many news publications, like the ones listed above, have a SecureDrop on their .onion sites. Onion sites (aka Tor sites) are websites only accessible on the dark web; you can’t view them using a regular browser. Their URLs (aka dark web links) have .onion as the domain, instead of the common surface web domains like .com or .net. Your safety on the dark web depends more on cautious browsing habits than any single security tool. While a VPN adds valuable protection, being selective about which sites you visit and never sharing personal information are equally important. Stick to verified dark web directories and legitimate services to minimize your exposure to risks.
TorVendor

In other words, these forums serve as advertising platforms for illicit services. Occasionally, data dumps containing credit card details or other sensitive information are also shared directly within the forums. Monitoring dark web forums is an important source for analyzing current cyber threats. Today, although threat actors broadcast their illegal activities via applications such as telegram, dark web forums are still one of the current content sources.

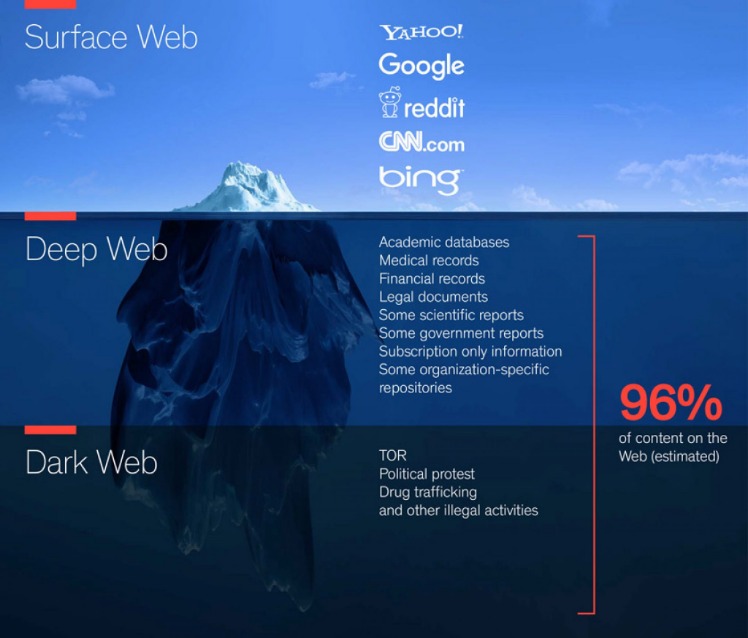
For those seeking anonymity or exploring decentralized services, the Tor network offers a hidden world of websites ending in “.onion” – inaccessible via standard browsers. Among the many tools available to guide users through this hidden landscape, OnionLinks.com has emerged as one of the most trusted and reliable directories for accessing .onion websites. Most dark web links are hosted on “.onion” domains due to the sensitive nature of the businesses or services they host. Tor websites may provide secure access to cryptocurrency wallets and anonymous email clients, and they’re also used to access black market sites. In the image above, (a) is the surface web, which includes publicly visible websites like blogs, shopping sites, and news sites.
How Can I Access A Dark Websites Safely?
Security researchers discovered a malicious package on PyPI called disgrasya, which included an automated card-testing script targeting WooCommerce stores. In a global enforcement operation, U.S. authorities seized over 145 domains tied to BidenCash, a major carding marketplace launched in March 2022. A single campaign may test thousands of cards within minutes, overwhelming servers and bypassing simple rate-limiting tools. I can’t say for certain, but I’ve always seen carding as a more ‘hardcore’ form of cyber crime—at least from a criminal’s perspective. Compared to harvesting phone numbers or email addresses, carding demands more risk, and potentially, more reward. For several years, Yahoo was at the apex as the internet’s best web service provider, offering…
Credit Card Monitoring Alerts
On one end, you’ll find links to independent journalism platforms like ProPublica’s .onion site and encrypted communication tools like SecureDrop. On the other, there are links to darknet markets, mixers, and carding forums—elements of the underworld that raise ethical and legal concerns. OnionLinks does not host this content directly, but by linking to it, it treads a gray area that reflects the broader debates surrounding online anonymity and regulation. It is first deep web prepaid cards seller and has been on the dark web since 2012. These cars are preloaded with funds means there is no previous owner. And can be used at any ATM, shop or online without worrying about hiding your identity.
Reddit is actually available on the dark web now, so there’s no need to rely on third-party tools to access it via Tor. Just bear in mind that the addition of anonymity to a platform like Reddit causes people to behave without a filter. However, for many, this appears to have been a simple publicity stunt, as they’ve since abandoned them.

Tor Guide
Onion.name is a dark web resource that helps make sense of the mess of letters and symbols that usually form the darknet sites. This tool rewrites dark websites into easily understandable texts. It has successfully become a replacement for AlphaBay Market, which was once leading the dark web transactions space. However, we do not recommend using this platform without taking proper precautions, such as anti-malware and a VPN. You can also use it on the surface web, but it is still unadvisable without proper safety measures. Just like Facebook, this is no random namesake; it is a legitimate platform from which to reach the CIA anonymously.
Popular Things You Can Purchase From The Dark
BlackCloud offers encrypted file storage specifically optimized for the Tor network. The service emphasizes privacy with zero-knowledge encryption and no registration requirements. My tests showed reliable performance for smaller files, but larger transfers can be slow due to Tor’s limitations. Facebook’s official dark web version helps users access the platform in countries where it’s blocked. During testing, I confirmed it provides the same functionality as the regular site while adding Tor’s privacy benefits. The interface works smoothly, but it usually loads slower due to Tor routing.
The use of cryptocurrency on dark web marketplaces has further facilitated carding operations. Cryptocurrencies such as Bitcoin and Monero provide a level of anonymity, making it difficult to track transactions. Businesses need monitoring activities in place, but at the same time, they should ensure that the monitoring complies with and adheres to all laws and regulations for implementing dark web monitoring. Some of the regulatory compliance measures include cyber best practices and data protection laws to ensure that monitoring is carried out for ethical as well as threat intelligence only. Perhaps one of the major attraction factors of these forums is undoubtedly anonymity. Cybercriminals want to carry out their illegal activities without detection by law enforcement agencies and other authorities.
Throughout this guide, we’ve explored the legal and ethical considerations of venturing into the dark web, how to enhance security and anonymity, and the criteria for identifying trustworthy resources. While no single tactic is foolproof, a layered approach—combining technical, operational, and psychological defenses—greatly improves your safety and confidence when navigating the dark web. One of the most insidious dangers on the dark web is not just technical malware or hidden exploits, but the human element—scammers and con artists who rely on psychological manipulation. Social engineering attacks leverage trust, fear, curiosity, or urgency to trick users into revealing sensitive information, transferring funds, or compromising their anonymity.