Dark net sites form a network that is protected by loads of encryption. Browsers like Tor (or The Onion Router) are able to peel back the layers of encryption, kind of like how you peel back the layers of an onion. Once it bypasses these layers, you get access to the content available on the dark web.
Best Practices For Browsing The Deep And Dark Web Safely
From a cyber-security perspective, it can be if you don’t know how to protect yourself. Non-technical people who are interested in satisfying their curiosity can quickly get into trouble. As such, you shouldn’t go looking around this area of the web unless you’re prepared and know what you’re doing. Additionally, the dark web can pose a threat even to those who don’t mess with it. The reason for this is because the primary transacted good is the data of users. There are gigabytes worth of information in the form of leaked data that is for sale.
How CrowdStrike Protects You From Illegal Dark Web Activity
- Besides, some additional protective measures may include application sandboxing, erase-on-shutdown, etc., based on a particular OS.
- Unlike traditional browsers, this will route your internet traffic through an anonymizing network and mask your IP address.
- On the other hand, the dark web uses darknets like Tor, Freenet, Riffle or other anonymized and encrypted networks as the underlying technology.
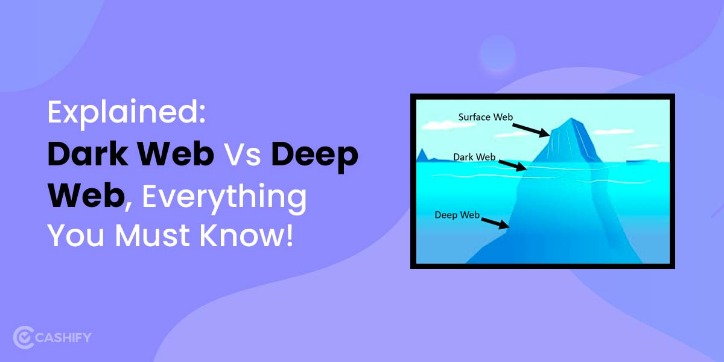
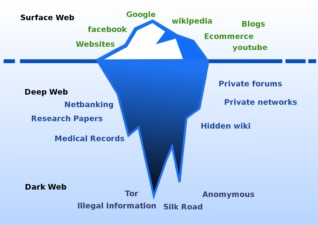
- The dark web, on the other hand, is defined as a subsegment of the deep web that can be accessed only with special tools.
- These Deep Web sites are not indexed by search engines, making them impossible to find via traditional search engines like Google, Bing, etc.
Additionally, contact the Social Security Administration to report the breach and discuss further protective measures. Norton 360 Deluxe provides a comprehensive suite of protection that can help block malware and dangerous links in real time, and even detect scams using cutting-edge AI detection. Plus, it features a built-in VPN to encrypt your connection, hiding your IP address and online activity, for more anonymous and private browsing. Many dark internet users favor Tor which uses a network architecture originally developed by the U.S. Naval Research Lab as a system of decentralized, anonymous nodes to enable anonymous online communication.
- While both the dark and deep web represent parts of the internet that fall outside the scope of traditional search engines, they differ in accessibility, use cases, and the types of threats they expose.
- By volume, the deep web constitutes approximately 90% of all internet content (according to Google’s documentation mentioned above).
- Understanding the Deep Web and Dark Web can help you navigate the internet with greater awareness.
- The deep web is part of your everyday web and thus has to comply with all sorts of security standards and be hosted by companies that have at least some interest in maintaining their users’ privacy.
- You’d also enjoy anonymity and privacy thanks to Tor’s encryption and routing, something you don’t get from most normal browsers.
Are There Legitimate Uses For The Dark Web?

A discrete online identity, which has nothing to do with your present one. Separate email, phone number, anonymous payment channel,…..the list can be long based on what you aspire to get involved with on the dark web. These operating systems send every outgoing request, not just the web browsing ones, through the Tor protocol, ensuring robust protection. Besides, some additional protective measures may include application sandboxing, erase-on-shutdown, etc., based on a particular OS. People use it to share information when their local governments act hostile or snoop extensively. For instance, Edward Snowden used the dark web to reveal that NSA surveils all US citizens, even if someone has no criminal history.
Is It Possible To Remove Personal Data From The Deep Web Or Dark Web?
The dark web marketplace is also fraught with malware, Malware-as-a-Service (MaaS) and stolen data (such as online credentials and credit card numbers) for sale. Basic online hygiene can prevent security lapses when accessing the deep web. For instance, using an unprotected public network to pay your bills might lead to cybercriminals being able to capture your payment information.
Start a free 30-day trial of Keeper Password Manager today to begin securing your accounts from common cyber threats on all parts of the internet. One dark web monitoring tool that works alongside Keeper Password Manager is BreachWatch®. BreachWatch monitors for suspicious activity on the dark web and alerts you as soon as any dark web activity matches the credentials stored in your Keeper Vault. When one of your records shows as “high-risk,” you’ll receive a notification and Keeper will help you change your password to one that is strong and unique. Dark net websites can only be accessed using designated browsers like Tor or I2P, and they’re different from those you come across on the surface web. For one, they usually don’t have any recognizable URLs, just a string of numbers and letters.
The 5 Best Free Password Managers Of 2025
Knowing the differences between the deep web and dark web can help protect your online safety when and if you choose to access each. Major differences between the two include accessibility, purpose, security level, content type, user intent, and possible legal implications. Most of what you see in search results is just a small slice of the internet. In fact, only about 4% of the web is indexed, meaning it shows up in standard search engines.
Why Do People Use The Deep Web?
This could be because the pages are not indexed, meaning they can’t be found by searching for them on search engines, they are paywalled websites or private databases. To access deep web content, you’ll need the direct link or sign-in credentials that grant you access to it. Special software is required to enter this network like the Tor browser, which is required to enter into Tor’s network. TOR can access regular websites also, a website on this network has .onion address.
Protect Your Personal Information While Browsing
Anything that does not show up on Google can be found on the deep web. Search engines crawl the internet through links, visiting one web page, the links on that page and so on, keeping track of all the information. What cannot be accessed by search engines is referred to as part of the deep web. The internet’s deeper layers—namely, the deep web and dark web—represent distinctly different realms of online interaction.
Because the dark web is home to all kinds of illegal activity, clicking on the wrong thing can place your device at risk of becoming infected with malware or other viruses. Malware is a type of malicious software that can spy on you, log your keystrokes and steal your personal information. As mentioned above, some common use cases for the deep web include accessing paid subscriptions and online accounts. However, since the dark web has to be accessed intentionally using the Tor browser and a VPN, most people won’t access the dark web in their day-to-day lives. According to Dataprot, a rough estimate is that the surface web makes up only 5% of the internet and the rest is made up of the deep web. The surface web is anything on the internet that you’re able to search for on standard search engines like Google.
If a particular website does not allow the crawlers to send the data for indexing, the site is not indexed and hence, cannot be seen on search engines. Behind the anonymity of the censor-resistant platforms, Dark Web has flourished a thriving trade of all that is illegal and unacceptable in civil society. In their book Cryptopolitik and the Darknet, researchers Daniel Moore and Thomas Rid claimed that around 57% of the Dark Web includes illicit content. Just to be clear, the Deep Web is hidden for a good reason, and unlike what many sensationalist reports on the subject have said over the years, it has literally nothing to do with illegal activity. With the Deep Web, if you’re accessing personal accounts or sensitive data, the primary risks are related to security and privacy breaches.
One must always respect the laws and regulations regarding privacy. The surface web, which is also called the visible web and the open web, is any website that search engines can add to their database. This includes websites, blogs, online product listings, and even public posts on social media.


