Engaging in illicit activities can lead to prosecution, as the law applies equally in this hidden part of the internet. Suspicious links and downloads pose a threat too, potentially leading to exposure to unwanted material or malware infections. Law enforcement’s presence, operating anonymously, aims to curb criminal activities, but it also underscores the dark web’s legal dangers.
- Well, there’s a reason why it’s recommended to browse with a minimized or rescaled window – you can be tracked based on your active window’s dimensions (yeah, they really can do that).
- Cybersecurity has to also cover everything physically on your computer too—which law enforcement or government authorities might have the right to seize if they come calling.
- So not only is your web activity hidden, but you can mask your IP address by connecting via a wide range of global VPN server locations.
- Other options include Ahmia and NotEvil, which focus on listing .onion links.
- Once connected to Tor, you’re ready to begin exploring the dark web.
- For example, your Geekflare.com—your trusted business resource for growth exists on the surface web.
If you want to learn all about privacy protection or cryptocurrency, the dark web has plenty to offer. There are a variety of private and encrypted email services, instructions for installing an anonymous operating system and advanced tips for the privacy-conscious. Dark web websites look pretty much like any other site, but there are important differences. Instead of ending in .com or .co, dark web websites end in .onion.
What Should I Do If My Social Security Number Is On The Dark Web?
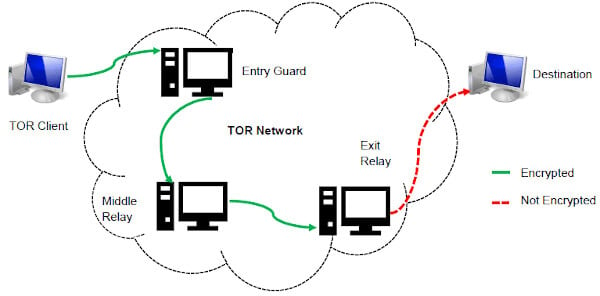
To review security settings, click on the onion logo in the top left and select “Security Settings”, which will bring up a slider offering a choice of the default of standard, or safer and safest. In “safer” mode, JavaScript is disabled on HTTP sites, some fonts are disabled, and all audio and video won’t run automatically, you’ll have to click to play. Slide up to the “safest” level, and as well as those settings, JavaScript is disabled on all sites. When you use the Tor network, your traffic is layered in encryption and routed via a random relay, where it’s wrapped in another layer of encryption.
Report It To The Authorities (if It’s Safe To Do So)
For instance, people can go on the dark web and post their thoughts about political activity without being reprimanded by government officials and other groups. Onion sites aren’t really dangerous, but they could be when accessed through unfamiliar or suspicious links. Your online activity and communications remain private and secret on the dark web. Because of this, some people use it to get around government restrictions, while others use it for illegal activities like smuggling drugs and weapons.
Legitimate Uses Of The Dark Web
The dark web marketplaces thrive on the demand for illegal services and extreme content. Your accidental visit to such sites can contribute to the perception of the demand, encouraging criminals to continue or expand their operations. The dark web hosts various types of illegal content, such as stolen data, child exploitation material, and prohibited items. As an average Internet user, you may accidentally stumble upon such content. Your access to illegal content, even if it is unintentional, can violate laws in many countries. Tor, short for The Onion Router, is a privacy-focused network that allows you to browse the Internet anonymously.
Illegal Content And Explicit Material
In addition, just surfing the dark web can unleash malware on your computer. Besides, governments might actively monitor such activity, and anyone showing a keen interest in the dark web can become a law enforcement target. Most of that is legal, like your financial information in banks, social media accounts, email archives, cloud storage, academic journals, streaming libraries, etc. Cybersecurity risk assessments and regular monitoring of dark web activities are essential to identifying and mitigating threats before they result in significant damage. While it empowers individuals to uphold freedom of expression and privacy, it simultaneously harbors activities that compromise security.
Darknet Communications In 2025 – From IRC Forums To Telegram Crime Networks
A limitation of this system is that websites cannot be dynamic (so they’re always simple static HTML pages). An often-quoted paper from the University of Michigan(new window) states that “public information on the deep web is currently 400 to 550 times larger than the commonly defined World Wide Web”. However, this paper was published in 2001, meaning these figures should now be taken with a heavy pinch of salt.
Is The Dark Web Legal In The USA
- Naval Research Laboratory, and the Tor Project, starting early 2000s, put this technology into the public domain, giving rise to the dark web.
- What’s more, they can also sell you personal information on the dark web as your personal data has a monetary value on the dark web.
- Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you’re looking for.
- The dark web, however, is a very concealed portion of the deep web that few will ever interact with or even see.
- This means you can go on the darknet privately while downloading torrents on the side.
Finally, because the dark web routes all traffic through a series of proxy servers, which are operated by thousands of volunteers around the world, the search process is typically very slow. Similar to using a standard web browser to access the open web, the act of using Tor or a dark web browser to access the dark web is not illegal in and of itself. It is illegal to perform illegal acts on the dark web, regardless of the level of anonymity provided by the platform. While the Tor network was not created for illegal activities, as it’s harder to trace websites to their physical location, cybercriminals have also adopted it to host their websites. Standard search engines index these websites and are accessible without special configuration.

Rule No.41 allows a federal judge to issue a search and seize warrant for any person who is using anonymity software like Tor. Then, simply click the operating system that you are using and download the file. While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store.

Additionally, you can opt for Subgraph OS as a second option to Tor. Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy. As listed above in our article, even respected organizations like the BBC and ProPublica have a version of their site on the dark web.
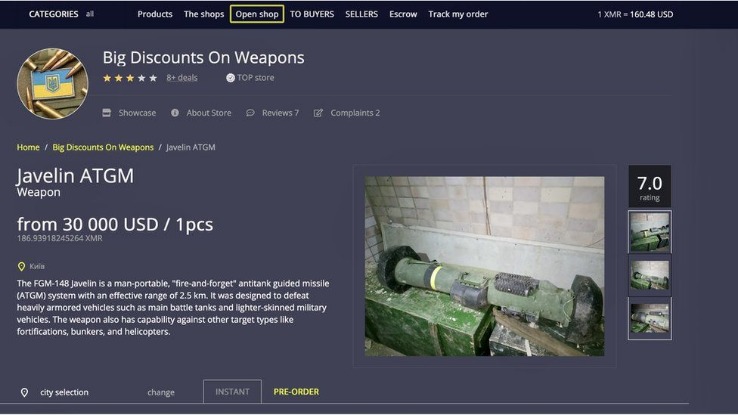
For instance, if you want to buy a laptop or a smartphone, you can try your luck in one of these shops. Sure, you can use other cryptocurrencies if Bitcoin’s not your cup of tea. Fortunately, in Hidden Wiki, every website is followed by a brief description so that the user knows what to expect. You can also take a look at the blogs & essays section if you want to find some nifty coding resources. At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen. A VPN hides your internet activity, making it harder for your connection requests to be traced back to you.

This bright side of the dark web chiefly includes whistleblowing and sensitive journalism. What we actually see, the surface, open, or visible web, just constitutes 5 to 10% of the total internet. Would you be able to tell if a cybercriminal changed one character to send you to a malware-infested copycat site? There are a lot of misconceptions about it, but we’ll answer that question once and for all in this guide. We’ll also discuss why it’s dangerous and why you should inform yourself about the dark web even if you don’t plan to be on it. Established in 2022, WizardShop is one of the biggest data stores on the dark web, focusing mainly on carding and financial data.

Each dark web is mutually exclusive and requires its own tools to access. Since Tor Onion Services is by far the most popular (and therefore most generally useful) dark web, we’ll focus on that here. Another important difference is that connections aren’t unidirectional. So (unlike Tor), outgoing and incoming traffic use different paths, making it much harder to trace a connection back to a user.
The point, however, stands — the deep web is much, much larger than the clear web. The dark web is much like the regular World Wide Web we’re all familiar with, except that the dark web provides much greater privacy. The internet is huge—even in its shadows—it is possible to wander legally there. Just because the dark web feels anonymous doesn’t mean it’s invisible—especially to U.S. authorities. Over the last few years, there’s also been a surge in ransomware gangs and cybercriminal groups using the dark web to leak sensitive information from American companies and agencies. Schedule a demo to see how Cyble can protect your brand from dark web threats.
In this volatile ecosystem, recognizing the dynamic nature of the dark web is half the battle. By acknowledging that services, communities, and security measures are in constant flux, you can better position yourself to respond effectively. One of the most insidious dangers on the dark web is not just technical malware or hidden exploits, but the human element—scammers and con artists who rely on psychological manipulation. Social engineering attacks leverage trust, fear, curiosity, or urgency to trick users into revealing sensitive information, transferring funds, or compromising their anonymity. By learning to recognize these ploys and adopting defensive habits, you can significantly reduce the risk of becoming a victim.