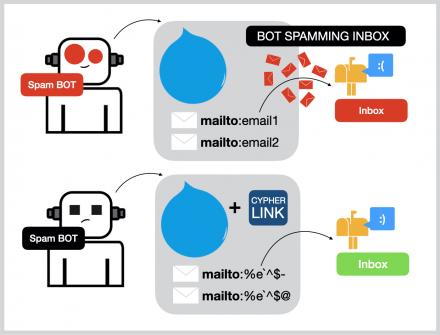
To mitigate risks, regularly scan for vulnerabilities utilizing tools like John the Ripper and exploit them effectively. Additionally, familiarize yourself with an instance of gogs and cryptographic concepts to decipher codes and progress through challenges more efficiently. Embrace these tools and techniques to enhance your skills in conquering Cypher challenges seamlessly. H25.io is a premium directory in the Tor network, offering access to a diverse and meticulously curated list of onion sites. Our mission is to simplify navigation in the complex and evolving world of the darknet.
Omg!Omg! Darknet Market
Grant SET PROPERTY privilege on a specified property, on all relationships with a specified type in a specified graph, to the specified role. Revoke MATCH privilege on all graphs and all nodes with either foo_label or bar_label and with a secret property that is null from the specified role. Grant READ privilege on all graphs and all nodes with a secret property set to false to the specified role.
Discover The Best Cypher Website Marketplace: Your Ultimate Cypher Onion Destination
This comprehensive writeup delves into each step of the penetration testing process, expanding upon initial reconnaissance with detailed analysis and exploitation. By thoroughly examining Cypher’s challenges, we not only enhance our cybersecurity skill set but also gain insights into real-world scenarios that mirror common organizational vulnerabilities. One crucial step in conquering Cypher challenges is identifying target services and ports. By conducting thorough reconnaissance, you can pinpoint vulnerabilities.
Compliance Ready

Despite hosting a relatively modest vendor base, it boasts an extensive selection of rare and distinctive items, outperforming conventional market assortments. 0xCipherLink ensures safe and encrypted file sharing using AES-256 encryption and PBKDF2 key derivation. With a user-friendly Tkinter interface, securely send and receive files over the network. Protect your data from online vulnerabilities with 0xCipherLink by 0x4m4. Launched after the takedown of AlphaBay in 2021, Abacus Market has rapidly risen to prominence.
List Operators
CipherLink is a versatile toolset designed for torrent management, piracy-related tasks, automated account creation, and more. Its modular architecture allows for easy extension because the code is easy to understand. This completes the full development lifecycle by linking an executable Cypher query against the specific question or scenario.
- It exclusively supports Bitcoin (BTC), Monero (XMR) for transactions, emphasizing the importance of privacy and security, and features a direct payment system for each purchase, catering to the needs of privacy-focused users.
- Deny TRAVERSE privilege on all graphs and all nodes with the specified label and with a secret property not set to false to the specified role.
- The date.statement() function returns the current DATE instant using the statement clock.
- The any() function returns true if the predicate holds for at least one element in the given LIST.
- Modify a standard database named topology-example in a cluster environment to use 1 primary servers and 0 secondary servers, and to only accept read queries.
Read Query
— The message contains unnecessary characters (such as spaces between each letter), which weakens the frequency analyses. However, we do not guarantee individual replies due to the high volume of messages. The website’s address can be found at the bottom of page 16 in The Book of Bill next to a copyright notice.1 Initially, upon entering the site, users were greeted by a black login screen and a triangle icon above it.

Super Market
Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more. CipherLink is a lightweight, high-performance communication library designed to provide end-to-end encryption for secure data exchange between clients and servers. Leveraging industry-standard AES-GCM encryption, CipherLink ensures the confidentiality and integrity of messages transmitted over the network.

At the input layer there are the coded messages (with ngrams), and at the output layer the different types of known and referenced ciphers on dCode. The AI encryption detection program is based on a multilayer perceptron (MLP). An MLP is a type of neural network composed of multiple layers of interconnected neurons, where each layer transforms the received input before passing it on to the next. This structure allows the program to detect subtle patterns in data, improve its accuracy, and adapt to different types of encryption more effectively. An encryption detector is a computer tool designed to recognize encryption/encoding from a text message. Grant SHOW ALIAS privilege to list aliases to the specified role.
Generate secure links for recipients to decode messages using the same encryption key. Cypher ventures boldly into an array of product categories beyond the commonplace, spanning drugs, fraud, hacking, counterfeits, and defense/intelligence sectors, each thoroughly categorized. While popular commodities like cannabis and stimulants are readily available, the marketplace excels in its ‘Other’ fraud section, presenting exclusive guides and tools.
Function returns the current LOCAL TIME instant using the statement clock. Cypher Market has quickly become a notable presence in the darknet marketplace, renowned for its minimalist design that prioritizes a seamless user experience. Upholding stringent ethical principles, particularly in prohibiting certain illegal content, Cypher sets a standard for responsible operation. Despite a relatively small number of vendors, it offers a vast range of unusual and unique items, surpassing traditional market offerings.
Use of this site constitutes acceptance of our User Agreement and Privacy Policy. The individuals are now facing some combination of narcotics trafficking, conspiracy, money laundering, and firearms charges that could lead to sentences of between 10 cypher market and 25 years in federal prison. Do you want to say that the email’s credentials have leaked, or you’re asking about something else? We are holding our third cypher market cloud startup showcase on Sept.
Registered Local Business Number
See both encoded and decoded versions simultaneously for quick verification and adjustments. One advantageous aspect of Cypher is its notably uncomplicated registration procedure, which solely necessitates the establishment of a username and password. The captchas employed by the platform are among the most straightforward, and the loading times of its pages are among the swiftest.
Fortifying Banking & Financial Services With
As we look to the future, we’re excited to integrate cutting-edge augmented reality (AR) technology into our cypher url marketplace. Imagine being able to visualize and interact with cypher url products in your own space before making a purchase. Our AR capabilities will revolutionize the way you shop, allowing you to see how items will look and fit in your environment, ultimately enhancing your overall cypher url experience. Embrace the future of cypher market shopping with our innovative AR features, and unlock a new level of convenience and confidence in your purchasing decisions.