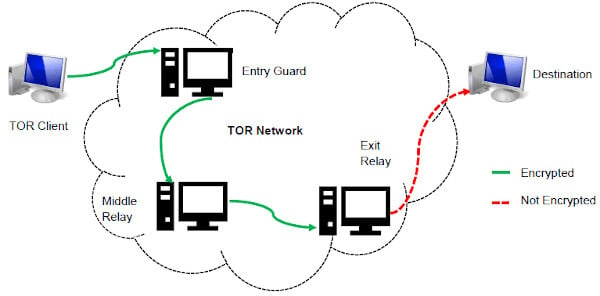
It adds an extra encryption layer and passes your traffic through a secondary server of your choice, preventing anyone from seeing that you are accessing the web via Tor. For this reason, you must watch out and avoid opening anything that looks suspicious to you. Many dark net sites do not undertake the necessary measures to protect users like most websites on the surface web. As a result, you can be exposed to different malware types, including botnets, ransomware, keyloggers, and phishing. Simply put, accessing and browsing the dark web is perfectly legal. For example, it maintains your privacy and enables you to access untraceable content and services.
Stand Up For Privacy And Freedom Online
The mobile app uses DuckDuckGo as its default search engine and is supported by the Orbit framework to provide secure access to the Tor network. Once a user installs a dark web browser on a device, it functions like a regular browser. That said, it can be difficult for users to find the material they are looking for on the dark web. Addresses tend to be a mix of random numbers and letters, making them challenging to remember or access manually. Addresses also change frequently due to the transient nature of many dark web actors.
Related Articles From The Safe Browsing Section
Additionally, forums facilitate the exchange of exploit kits and zero-day vulnerabilities, which can be weaponized before patches are released. The anonymity of the dark web makes it a fertile ground for coordinating cyberattacks and sharing illicit services without detection. These sites offer access to illegal streaming of pirated movies, TV shows, sports events, or other copyrighted content, often in high quality. These sites bypass copyright protection and may be accessed only on the Dark Web to avoid legal scrutiny. The dark web is content that exists on dark nets, which require specialized software (like the Tor Browser), configurations and authorization to access.
Monitor System Resources
For some users, portions of the deep web offer the opportunity to bypass local restrictions and access TV or movie services that may not be available in their local areas. Others go somewhat deeper to download pirated music or steal movies that aren’t yet in theaters. Advocacy groups are also reaping the advantages of the darknet because, here, the term of censorship is as popular as HTTPS. It makes up about 6% of the internet, and it’s where you find everything from illegal marketplaces to forums for whistleblowers. To contribute a tip, join the community, which can be done anonymously through an approved onion link. The site is strongly resistant to hackers and encrypts your data in transit as well as the rest.
What Is The Dark Web & How To Access It Safely In 2025
For anyone considering exploring the Dark Web, it’s crucial to tread with caution. But for those seeking privacy, freedom of expression, or simply a glimpse into this hidden world, the Dark Web is a fascinating, albeit dangerous, place to explore. Cryptocurrency, particularly Bitcoin, plays a significant role on the Dark Web.
Common Scams On Dark Web Marketplaces
- The platform stood out during my testing for its commitment to anonymity — all messages are fully encrypted and stored on a decentralized network.
- That’s helpful because Tor can suffer IP leaks and malicious actors can run Tor servers.
- Contrary to a widespread misconception, the dark web is a tiny part of the web.
- Because Tor is very slow, many dark web-only websites avoid complex designs and fancy graphics to deliver a faster experience.
- It has a vast library of over 1.5 billion indexed pages that lets you find whatever you are looking for.
- Add to that the fact that Bitcoin is the preferred currency on the dark web.
However, you can still take illegal actions within Tor that could incriminate you regardless of the browser’s legality. You could easily use Tor in an attempt to pirate copyrighted content from the deep web, share illegal pornography, or engage in cyber terrorism. Using a legal browser will not make your actions fall to the right side of the law. Understanding that the nature of the internet meant a lack of privacy, an early version of Tor was created to hide spy communications. Eventually, the framework was repurposed and has since been made public in the form of the browser we know today. The dark web was once the province of hackers, law enforcement officers, and cybercriminals.
Does The CIA Have An Onion Site?

Some may lead to malicious sites, downloading malware on your device. Onion sites are far safer to use as they are hidden deep within the deep web. Also, since users can only access them using the Tor browser (with its high-end encryption), users can be rest assured their identities and locations remain hidden.

While it empowers individuals to uphold freedom of expression and privacy, it simultaneously harbors activities that compromise security. Beyond DuckDuckGo, other options have failed to keep up with the evolving landscape. Though these browsers are effective at serving up dark web search results, the experience is reminiscent of browsing the web in the late 1990s. To access the dark web, you need an anonymizing web browser or any browser that supports the Tor network. The Tor Browser is the most popular browser for the dark web, but other popular options exist, like Brave, Comodo Dragon, Epic and SRWare Iron. Keep in mind that in some regions like China and Russia, it’s illegal to use anonymizers.

ZeroBin has a cool autodestruct feature that makes the message go kaboom (not literally) after the recipient reads it. In this sequel, I’m going to show you some of the not-so-clear-web’s hidden Easter eggs and how to get there. So, without delay, let’s step into the onion patch aka the best 20 dark web websites. So, you took my course on how to get on the dark web and want to explore your newfound superpower? To access the dark web, you will need the Tor browser, which provides the necessary anonymity and security.
- This makes AHMIA a relatively safe way to access content on the dark net.
- Content and services on the deep web are accessible through a regular browser.
- Some countries and ISPs may try to prevent access to DuckDuckGo’s direct link.
- The current repository has over 20,000 journals with over 10 million articles across all subjects.
- You’ll find websites selling stolen credit cards, lists of social security numbers , forged documents, counterfeit currency, weapons, and drugs.
- DuckDuckGo’s approach to search is built on the premise that personal information should remain private and that users should not be profiled based on their search queries.
The files are automatically encrypted, and the sender’s IP is not logged. Tor Links is a backup directory of “.onion” sites in case other directories go offline. The best Tor sites are under constant threat of closure, including Tor directories like the Hidden Wiki, so having a backup in case one goes down is handy.
Illegal Content And Explicit Material
When you create a free Proton account, you get encrypted email with 1 GB storage, two password vaults, and one VPN connection. At $9.99/month, you can migrate to a premium plan with 500 GB storage and unlimited messages. Unlock the secrets of dark web websites real and learn how to explore them safely with essential tips and resources. Your activities on the dark web are not entirely shielded from tracking, and relying solely on anonymity can lead to a false sense of security. The dark web draws not only serious cyber criminals but also law enforcement agents aiming to catch them. Many exit nodes are actually operated by law enforcement and scammers.
Resources
For an extra sense of security, try a powerful identity theft protection service like LifeLock Standard that offers dark web monitoring. LifeLock notifies you if we find your personal information on the dark web, and we’ll help you run damage control with assistance from legal experts and recovery specialists. DuckDuckGo is built into the Tor browser, making it a convenient option for looking up dark web websites. However, before you start your search, toggle the button beside “Onionize” to anonymize your session. This hides your activity and personal identifiers so you can browse safely, protected from prying eyes and identity theft. From its inception, Ahmia has been committed to ethical principles, filtering out content related to child pornography and maintaining a blacklist to mitigate abusive services.
Tor was initially developed by the US Navy to facilitate secure communication for informants. Similarly, the CIA launched its .onion site to provide worldwide anonymous access to its resources. It serves the same purpose as ProPublica – facilitating access in countries where it may otherwise be restricted. Facebook’s onion portal is an essential communication tool for people living under oppressive regimes, despite the social media giant’s controversial reputation when it comes to privacy.
The dark web is not easily accessible, especially with browsers like Chrome or Safari, as it requires specialized protocols like Tor’s onion routing. As a result, the recommended browser for accessing the dark web is the Tor (The Onion Router) browser. Dark web forums are online platforms that can only be accessed using anonymous networks, mainly Tor…. It hosted over 7,000 .onion categorized links to make surfing the web easier.
We review and list tools and products without bias, regardless of potential commissions. The federal investigation which uncovered and shuttered the first dark web site, also led to the closure of three others. “The leadership team that operated one of the sites also operated several of the others.” The takedown of dark web leaders and users also included the convictions of men from Virginia, Maryland, Indiana, Texas, Washington, Arkansas, Michigan and Oklahoma. Galeotti said, “We luckily have very sophisticated prosecutors and agents who work specifically on this kind of thing. These are people who have a more of a technical understanding.”