By tapping theirNFC-enabled device or card at a point-of-sale terminal, customers canautomatically register their purchases and accumulate points withoutneeding physical loyalty cards or following lengthy processes. Cybercriminalsalso sell e-SIM contracts to activate the Internet on POS terminalsand communicate with payment gateways. These contracts can beactivated by money mules or registered under fake details. Some ofthe e-SIM offerings have been observed to originate from Hong Kong,Japan, and the United States. Manycybercriminal activities in China are believed to be part of largerorganized crime syndicates that are state-sponsored,state-encouraged, or state-tolerated.
With the right strategies, even the most sophisticated cyber threats become manageable challenges rather than insurmountable obstacles. Meet Alex—a freelance graphic designer who prided himself on his tech savviness. However, further investigation revealed that his card information had been compromised in a data breach months prior. Alex’s story serves as a reminder that even the most cautious consumers can fall victim to sophisticated cyber theft. Not only did he face immediate financial setbacks, but the recovery process took weeks, involving disputed charges, delayed client payments, and a temporary dent in his credit score.
Million Stolen Credit Cards To Be Released For Free By B1ack’s Stash Marketplace
Unless you live the rest of your life only paying with cash, you’ll never be totally impervious to payment fraud. One of the largest known underground shops, Joker’s Stash, generated more than $1 billion before getting shut down in February, according to Gemini Advisory. A 2019 data leak of another shop, BriansClub — which appears to have been by a competitor, according to Threatpost —shows how pervasive this trend has become. All content provided on Web Design Booth is for informational purposes only and does not constitute professional advice.
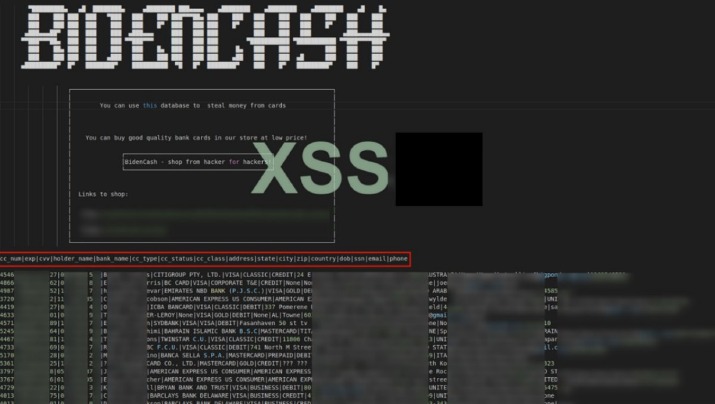
Join us as we break down and discover the methodologies of card fraud using our dark web monitoring tool, Lunar. Judging from the activity on the shop, BidenCash appears to be thriving in 2023, providing an active data and money exchange platform in a market that has experienced a decline in recent years. This time, the leaked data contains card numbers, expiration dates, and three-digit security codes (CVVs). The expiration for most cards reviewed by BleepingComputer ranges from 2025 to 2029, but we also spotted a few expired entries from 2023. Contrary to popular belief, most carding platforms no longer hide in the dark web (i.e. the Tor network). The sites I’ve evaluated this year all had clear web addresses—with ‘.onion’ versions available for some of them.
Impel Global: Transforming Financial Messaging And Payments Through Blockchain Precision
It is important to note that engaging in transactions on the Dark Web carries significant risks, and using payment methods that cannot be traced back to the buyer does not guarantee complete anonymity. Despite the pseudonymous nature of cryptocurrencies, law enforcement agencies and cybersecurity experts have developed sophisticated techniques to trace these transactions. Unlike the traditional web we use every day, with search engines indexing websites for easy discovery, the Dark Web operates on anonymous networks such as Tor. This anonymity allows criminals to conduct illegal activities without fear of being traced by law enforcement agencies.
Top Strategies For Risk-Based Transaction Monitoring
Engaging in illegal activities can lead to severe legal repercussions, including fines and imprisonment. Moreover, the financial repercussions for victims of credit card fraud can be devastating. Remember, while evaluating seller feedback and ratings can provide valuable insights, engaging in credit card transactions on the Dark Web is illegal and carries significant risks. It is essential to proceed with caution and prioritize personal security and ethical considerations. Remember, accessing and participating in Dark Web marketplaces is illegal and rife with risks.
Telegram Carding Groups
- The digital world is as exhilarating as it is fraught with risks, and the dark web’s role in the world of stolen credit card data is a stark reminder of that duality.
- Sales of passports, driver’s licenses, frequent flyer miles, streaming accounts, dating profiles, social media accounts, bank accounts, and debit cards are also common, but not nearly as popular.
- When fraudulent transactions occur, merchants frequently end up eating the costs through chargebacks.
- Remember, while evaluating seller feedback and ratings can provide valuable insights, engaging in credit card transactions on the Dark Web is illegal and carries significant risks.
So, the actor, to prove his identity, must provide a photo with himself holding an ID, like a passport or driver’s license, along with the bank account information. Kim Komando hosts a weekly call-in show where she provides advice about technology gadgets, websites, smartphone apps and internet security. Credit card details with balances up to $5,000 go for $110, and online banking logins with $2,000 or more go for $60. Actual or formally correct ID card numbers are among the most expensive goods on the dark web. Interestingly, a major part of the carding ecosystem revolves around education.
Whether you’re a savvy digital native or just starting to navigate online transactions, these practical strategies can keep your financial health in check. Kaspersky advises individuals and organizations monitor bank notifications, enable two-factor authentication and run full security scans on all devices to remain vigilant against these types of malware threats. When Torrez closed in December it was one of the largest English-language marketplaces in the world selling drugs, hacking tools, counterfeit cash and criminal services. Surfing on the dark web, communicating, or transferring private information is legal. However, buying credit card information from the dark web is illegal and leads to severe penalties from the government.

Credit Card BasicsThing To Know About Data Breaches
Scammers start by prompting users to download malware, which is often disguised as a harmless email attachment. Once it starts running on your machine, the malware collects data such as used keystrokes, browser history, and shopping habits. Collecting used keystrokes is how hackers typically guess credit card numbers, PINs, and passwords. Using a public Wi-Fi network for payments is a major security risk as hackers can easily intercept the transmitted data. Unsecured Wi-Fi networks are prone to man-in-the-middle attacks, where a hacker intercepts the exchange between two parties—often by compromising the router—and gains access to sensitive data. Using an unsecured WiFi network, such as one that is public, can place all of your sensitive data at risk due to Man-in-the-Middle (MITM) attacks.

The Human Element In A Digital Heist
MITM is a type of cyber attack where a cybercriminal intercepts the data being sent between two people. A MITM attack most commonly occurs on public WiFi networks because they’re left unsecured and anyone can connect to them. Data breaches can happen for a number of reasons such as an employee making an error or a cybercriminal launching a successful cyber attack. When public data breaches occur, cybercriminals will collect as much data as they can and publish it on the dark web for others to view or buy. Now that we have covered the necessary steps to access the Dark Web safely, let’s move on to the process of buying credit cards on the Dark Web.
Collecting Threat Intelligence
Dark web credit cards are typically sold on online marketplaces that are only accessible through the Tor network. These marketplaces are often referred to as “carding forums.” Buyers can purchase credit card numbers using cryptocurrencies like Bitcoin. One such forum was seen offering to give away a million credit cards for free just as a marketing exercise, for goodness sake. Now Kaspersky threat intelligence specialists have revealed the extent to which infostealer malware and bank card theft go hand in hand. The dark web credit card market represents a significant threat to individuals and financial institutions alike.

Here’s to making savvy, well-informed choices in an era where every swipe, click, and tap has the power to shape your financial destiny. They employ reputation systems, encrypted transactions using cryptocurrencies, and detailed product listings. However, unlike mainstream sites, these platforms operate in complete anonymity and outside legal oversight. So next time you swipe your card or tap your phone at checkout, spare a thought for the high-tech battle that keeps your money safe in an era where your data’s value could rival a blockbuster movie plot. Even if a cybercriminal manages to snag your password, an additional layer of authentication—be it a fingerprint, text message code, or an authentication app—significantly raises the barrier to entry. The most expensive card details, which cost about $20, were in Hong Kong and the Philippines and the cheapest, some at just $1, originated in Mexico, the US and Australia.
A compromised online account is an account that has been accessed without the permission of the person who owns it. Accounts are often compromised due to weak password practices like using short passwords or reusing passwords across multiple accounts. When engaging in any transaction, it is essential to take protective measures and precautions to safeguard personal information and privacy. This includes using a secure and anonymous internet connection, using a reputable VPN (Virtual Private Network), utilizing trusted marketplaces and vendors, and practicing good online security hygiene. It is important to note that engaging in such activities is illegal and unethical. The financial repercussions for victims can be debilitating, leading to damaged credit scores, fraudulent charges, and identity theft.

You only need to contact one credit reporting firm to initiate a fraud alert, which in turn is legally obligated to share your notice with others. In addition to a clearnet domain, they also shared the new URLs through various hacking and carding forums. The answer lies behind distributed denial of service (DDoS) attacks that targeted its original domains. As a result, in order for word to get out in regard to fresh URLs for the service, the hackers are distributing the data free of charge.


