To check, you can use dark web scanning or breach detection tools like Avast Hack Check or LifeLock Breach Detection to search for compromised data. If found, take immediate steps to secure your accounts and personal information. Researchers from Recorded Future estimated that while there are more than 55,000 existing onion domains, only 8,400 (or roughly 15%) of these sites were active. So, when measuring the total network of live dark web sites alongside the surface web, only about 0.005% of the internet is the dark web.
Is The Dark Web Illegal? Everything You Need To Know
Anyone running a malicious exit node could potentially monitor, manipulate, or inject content into your session, especially if you’re visiting non-HTTPS sites. When selecting a VPN service, it’s important to choose a reputable and reliable provider. Look for VPNs that have a strict no-logs policy, meaning they do not store any information about your online activities. Additionally, ensure that the VPN service has a wide network of servers in various locations to offer you more options for server locations. It’s important to note that not everything on the Dark Web is illegal. Whistleblowers, for example, may use the Dark Web to anonymously share sensitive information with journalists or law enforcement agencies.

Accessing The Dark Web
I2P, or the Invisible Internet Project, is an anonymous network layer to facilitate secure and private communication among its users. It works as a decentralized, peer-to-peer network that emphasizes censorship resistance and complete anonymity. The surface web is the open part of the internet, which includes publicly accessible websites and resources. Search engines index all the web resources on the surface web, so you can search for them online.
A Quick Guide On How To Use A VPN With Tor
As such, you should exercise caution when accessing any unofficial dark websites. The dark web contains much of the internet’s illicit content, ranging from drug trafficking to child pornography sites. After all, it’s much less popular, can’t be used to access normal websites, and isn’t as easy to use, among other disadvantages.
Top VPN Deals
DuckDuckGo uses its web crawler and also curates data from over 400+ sources, including Google and Bing. Hence, you’ll see accurate search results similar to searching on Google. This guide dives deep into Tor, explaining how it works, its pros and cons, and how to utilize it to protect your online privacy.

It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security. Get the latest in privacy news, tips, tricks, and security guides to level-up your digital security. As well as phishing scams, a multitude of other scams operate across the dark web. There are many fake marketplaces and platforms that might offer to sell you goods or services but actually take your money without providing anything in return. Since the dark web is unregulated, there’s almost nothing scam victims can do to seek justice or compensation. Let’s look at two popular browsers you can use to access the dark web on desktop computers and laptops.
Illegal Content And Explicit Material
Many mainstream media organizations monitor whistleblower sites looking for news. Dark web commerce sites have the same features as any e-retail operation, including ratings/reviews, shopping carts and forums, but there are important differences. When both buyers and sellers are anonymous, the credibility of any ratings system is dubious. Dark web search engines exist, but even the best are challenged to keep up with the constantly shifting landscape. The experience is reminiscent of searching the web in the late 1990s. Even one of the best search engines, called Grams, returns results that are repetitive and often irrelevant to the query.
The goal is to minimize any potential damage if you accidentally stumble upon harmful content or download something malicious. Unlike the clear web, where websites are often rated or reviewed, most dark web sites are unregulated. This is why it’s important to visit only well-known, reputable sites with a history of providing safe, reliable information or services. The history of the Dark Web is intricately tied to the development of internet technology and the ongoing pursuit of online anonymity. The concept of an encrypted, hidden layer of the internet began taking shape in the 1990s. The U.S. Naval Research Laboratory developed the precursor to the Tor (The Onion Router) project during this period as a means to protect government communications.
What Is The Onion Network?
- To surf the web privately, you need to connect to the Tor network from your browser.
- I am CyberBestPractices, the author behind EncryptCentral’s Cyber Security Best Practices website.
- It operates within a network of encrypted websites that require specific software, configurations, or authorization to access.
- The dark web is like the mysterious basement of the internet — dimly lit, a little spooky and filled with stuff you probably shouldn’t touch.
- Threat actors also exploit vulnerabilities in your systems and software to gain access to them.
- Tor Browser has since become a popular tool of journalists, activists, and others that may be subject to being monitored online.
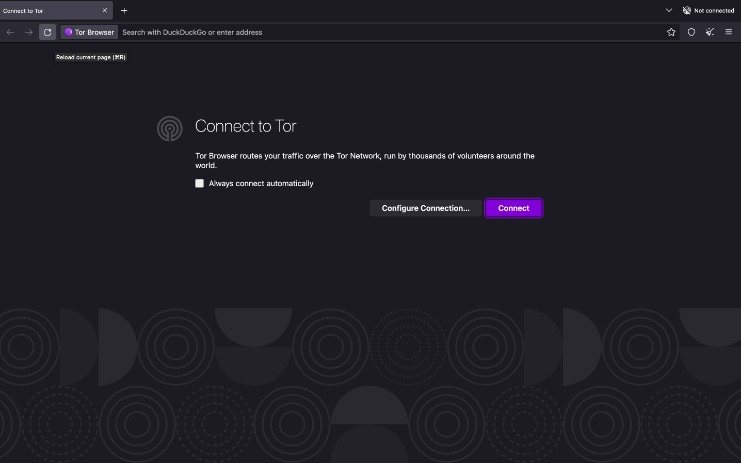
The privacy offered by the Tor browser is important in the current digital age. Corporations and governing bodies alike currently participate in unauthorized surveillance of online activity. Some simply don’t want government agencies or even Internet Service Providers (ISPs) to know what they’re looking at online, while others have little choice. Users in countries with strict access and user laws are often prevented from accessing even public sites unless they use Tor clients and virtual private networks (VPNs). The Tor Browser provides anonymity and privacy by routing your internet connection through a network of volunteer-operated servers around the world. This process, known as “onion routing,” masks your IP address and encrypts your data, making it difficult for anyone to trace your online activity.
Its VPN Accelerator distributes the CPU load between multiple processes in OpenVPN, and modifies the servers’ Linux stacks to shorten the normal packet processing path. All Surfshark servers are RAM-only and support the WireGuard, IKEv2, and OpenVPN protocols. The company operates a strict no-logs policy and protects internet traffic using AES-256-GCM encryption together with a SHA512 authentication hash and 2048-bit DHE-RSA key exchange.
- They can sometimes identify users through other methods, such as monitoring behavior, exploiting vulnerabilities or conducting undercover operations.
- You can use the VPN rated #1 for the dark web with no restrictions for a month—great if you want to try this no-log provider’s Onion over VPN servers for yourself.
- Be cautious of random or obscure links — these could lead to dangerous or malicious websites.
- While TOR offers substantial anonymity, using a VPN in conjunction with the TOR Browser can enhance privacy.
- It creates a space for staying anonymous, which itself is kind of a double-edged sword.
- The dark web is not meant for the general public since it is harder to access and need technical knowledge.
Maintain Anonymity
Surfshark is a low-cost provider that ticks all the boxes for use with the dark web. It has a large network of secure servers, the ability to keep connections private, and apps that are rich in security features. Using a VPN in conjunction with the Tor (The Onion Router) browser is the best way to access the dark web safely. A dark web VPN prevents websites and your ISP from knowing when you’re using the Tor browser.
If you need to access dark web resources, these are the steps you need to take. However, the dark web has far more uses for organizations and individuals than what a small subset of criminals do under its umbrella. Here’s everything you need to know about this other internet, as well as how to access it. The area of the internet we access daily is known as the clear or surface web. The internet opened the door to a realm of possibilities that permanently changed the business landscape and our personal lives. In a world of bulk data collection, surveillance, and personalized ad tracking, it’s up to us to take control of our personal privacy.